Trezor
Trezor homepage: Trezor.io

Trezor is a hardware wallet providing advanced security for handling Bitcoin and other cryptocurrencies private keys.
Unlike traditional cold storage methods (offline storage or paper wallets), Trezor makes secure payments without exposing your private keys to a potentially compromised computer. See Security philosophy for more info.
Trezor hardware wallets

Trezor makes three different hardware wallets:
Trezor One offers everything needed to protect cryptocurrency funds together with advanced features like Password manager or U2F two-factor authorization.
For more information, see Trezor Model One on the Trezor website.
Trezor Model T is the premium version of the hardware wallet. In addition to the functionalities of Trezor One, it has a colored touchscreen for secure on-device input, modern design, an SD card slot, and some other more advanced features.
For more information see Trezor Model T on the Trezor website.
Trezor Safe 3 is a newer hardware wallet created by Trezor in 2023. It resembles the Trezor T, but features two buttons below the screen, an EAL6+ secure element, a USB-C connection, a newer OLED display, and metal backup for your seed phrase.
For more information see Trezor Safe 3 on the Trezor website.
See also this comparison table.
How does it work?

Trezor is a small single-purpose computer. It is designed to protect your private keys from possible online and offline risks. To do this, Trezor keeps the private keys away from the Internet and confirms the transactions in-device. That way, you can always check the screen for the right address, amount and transaction fee before sending your bitcoins.
In layman's terms, you can connect Trezor to an infected computer and still be able to have 100% control over the funds in your device.
Find out how exactly Trezor is designed to provide excellent security:
Mitigations against threats
Trezor maintains a list of attack types it protects you from on its web page, and how to protect against them and what to do in dangerous situations.
Below is a summary of each threat and the mechanisms used by Trezor to protect from each of them.
Brute forcing the PIN
Trezor devices force a user to wait double the amount of time between failed unlock attempts. For instance, 1 second after the first attempt, 2 seconds after the second attempt, and 4 seconds after the third attempt. The device automatically wipe itself after 16 failed PIN entry attempts.
Reflashing with malicious firmware
After a firmware reflash, the Trezor device storage is automatically wiped, and a warning is displayed on the screen to the user during startup if the firmware is not signed by Satoshilabs.
Evil maid attack
Evil maid attacks are when an adversary replaces your hardware wallet with a fake device with additional hardware for transmitting sensitive data. Hardware wallets can resist evil maid attacks but can't entirely prevent them. Trezor recommends signing the back of your device with a permanent pen, or setting a custom home screen with a unique picture that would be hard to copy.
Address hijacking
Hardware wallets cannot prevent malware from replacing a crypto address in the clipboard with its own address, because this operation occurs on the computer. You must double-check the address pasted into your wallet with the one on the payment page before broadcasting the transaction.
Honeypot token scams
This is a type of scam that occurs on some altcoins where the scammer creates a token and writes code that prevents it from being sold except by select addresses. Trezor devices do not currently warn about this scenario. It is advised to use websites that can detect honeypot tokens such as Honeypot.is or Token Sniffer before buying unknown tokens.
Side channel attacks
In Elliptic curve cryptography, it is possible to guess the private key of an address by monitoring the power usage of the CPU during the point multiplication operations. This is possible because the multiplication step of the algorithm takes relatively longer than the addition step, allowing for an adversary with physical access to the computer to reliably determine the positions of binary 1's and 0's in the private key.
These vulnerabilities are resolved by using constant-time point multiplication algorithms. Bitcoin Core and several wallets use this procedure, including Trezor devices.
Hacking Trezor servers
Trezor allows you to set up a custom backend server for the Trezor Suite software in case Trezor servers get hacked.
Using Trezor
Trezor Suite is an easy-to-use interface for Trezor. Using the Suite, you can easily set up the device, manage your cryptocurrency assets, initiate transfers to other services or friends, and more. It is also possible to use your Trezor device with other wallets, eg., Electrum.
Sending transactions
Have a look at how easy and comfortable it is to send transactions:
Receiving address phishing protection
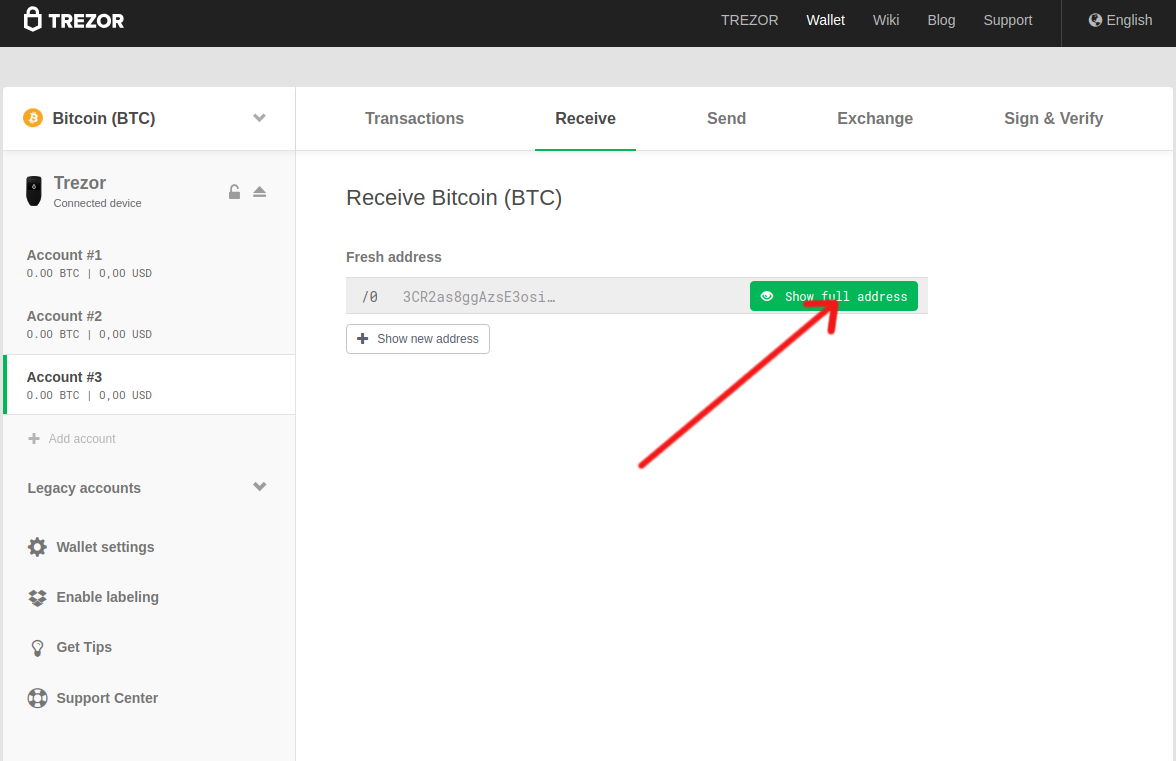
Make sure that an infected computer has not changed the receiving address you have provided to someone else. The "Show on Trezor" feature has been developed specifically for this purpose:
Sign & Verify messages
It is also possible to sign and verify messages using Trezor:
Backup and recovery
When first activating the device, you are asked to write down the recovery seed phrase.
This means that in case your Trezor is lost or stolen you can easily retrieve your funds another Trezor or any other compatible wallet.
Advanced Settings - Passphrase
You can further improve the security by using a passphrase and or multiple passphrases to create so-called "Hidden Wallets". More details here:
Advanced features
- U2F / FIDO2
You can use Trezor as your U2F and FIDO2 token with services such as Google, GitHub or Dropbox. A further advantage of Trezor is that its users can truly verify what they are about to authorize on the device display.
- Password Manager
The Trezor Password Manager allows users to manage all their passwords and digital identity with the Trezor security and encryption. The Trezor Password Manager does not require remembering one master password, as access is granted by pressing a physical button on your Trezor device. Your passwords are stored on Dropbox or Google Drive in an encrypted form using the private keys derived and safely stored in your Trezor.
- SSH login
With the Trezor SSH Agent, administrators can enjoy passwordless and secure authentication to their servers.