Securing your wallet
Introduction
Wallet security can be broken down into two independent goals:
- Protecting your wallet against loss.
- Protecting your wallet against theft.
In the case that your current wallet hasn't been protected adequately (e.g. put online with a weaker password):
- Making a new secure wallet, using appropriate long-term protection.
Technical Background
Bitcoin transactions send Bitcoins to a specific public key. A Bitcoin address is an encoded hash of a public key. In order to use received Bitcoins, you need to have the private key matching the public key you received with. This is sort of like a super long password associated with an account (public key). Your Bitcoin wallet contains all of the private keys necessary for spending your received transactions. If you delete your wallet without a backup, then you no longer have the authorization information necessary to claim your coins, and the coins associated with those keys are lost forever.
The wallet contains a pool of queued keys. By default there are 100 keys in the key pool. The size of the pool is configurable using the "-keypool" command line argument. When you need an address for whatever reason (send, “new address”, generation, etc.), the key is not actually generated freshly, but taken from this pool. A brand new address is generated to fill the pool back to 100. So when a backup is first created, it has all of your old keys plus 100 unused keys. After sending a transaction, it has 99 unused keys. After a total of 100 new-key actions, you will start using keys that are not in your backup. Since the backup does not have the private keys necessary for authorizing spends of these coins, restoring from the old backup will cause you to lose Bitcoins.
Creating a new address generates a new pair of public and private keys, which are added to your wallet. Each keypair is mostly random numbers, so they cannot be known prior to generation. If you backup your wallet and then create more than 100 new addresses, the keypair associated with the newest addresses will not be in the old wallet because the new keypairs are only known after creating them. Any coins received at these addresses will be lost if you restore from the backup.
The situation is made somewhat more confusing because the receiving addresses shown in the UI are not the only keys in your wallet. Each Bitcoin generation is given a new public key, and, more importantly, each sent transaction also sends some number of Bitcoins back to yourself at a new key. When sending Bitcoins to anyone, you generate a new keypair for yourself and simultaneously send Bitcoins to your new public key and the actual recipient's public key. This is an anonymity feature – it makes tracking Bitcoin transactions much more difficult.
So if you create a backup, do more than 100 things that cause a new key to be used, and then restore from the backup, some Bitcoins will be lost. Bitcoin has not deleted any keys (keys are never deleted) – it has created a new key that is not in your old backup and then sent Bitcoins to it.
Making a new wallet
In the case that a wallet has been distributed, or stored, in a (real or potential) compromised state, it is wise to create a new wallet and transfer the full balance of Bitcoins to an address contained only in the newly created wallet.
For example, this will be necessary if one created a wallet with a password of 12 characters, as suggested. However a few years have passed and the wallet is now more easily compromised. Just re-encrypting isn't secure. One needs to make a new wallet and make the old wallet worthless (spending the funds to the new wallet).
Making a secure workspace
Linux
The first step is to make a new user, so run:
adduser new_user_name
as root. When you get to the prompt 'Enter the new value, or press ENTER for the default', just keep hitting ENTER.
Then switch user to the new user. To get to the new user you can use the switch user icon for your system, which on Ubuntu is in the 'System/Quit' screen, or if there is no switch icon on your system you can log out and log back in as the new user. Then click on a folder in the new user to display the file browser, then keep going up folders until you see the new user home directory, then right click to bring up the Properties dialog, then click on the Permissions tab, then in the Others section, set the folder access to None.
For secure browsing, open Firefox, and then go into the Edit menu and click Preferences. Starting from the left, click on the General tab, and in the 'Startup/When Firefox starts' pop up menu, choose 'Show a Blank Page'. Then click on the Content tab, and deselect 'Load images automatically' and deselect 'Enable Javascript'. Then click on the Privacy tab, and in the 'History/Firefox will' pop up menu, choose 'Never remember history'. Then click on the Security tab, and in the Passwords section, deselect 'Remember passwords for sites' and deselect 'Use a master password'. Then click on the Advanced tab, then click on the Update tab, and then in the 'Automatically check for updates to' section, deselect 'Add-ons' and 'Search Engines'.
When javascript is disabled, the linux download page will not download automatically, so you'll have to click on the 'direct link' part of the "Problems with the download? Please use this 'direct link' or try another mirror." line.
After you've made your secure new user, to maintain security you should use it only for bitcoin.
It's also a good idea to encrypt the Home directory of whatever user you run Bitcoin under using ecryptfs-utils. To do this:
- If the Home directory is not empty you should back it up first, by just copying the data to an external drive or something.
- install ecryptfs-utils (on Ubuntu: sudo apt-get install ecryptfs-utils)
- log out of X (graphical system) and press Ctrl+Alt+F1 to login to the command shell (you must be logged out or some files will be open and the tool won't be able to encrypt your data)
- change directory to something that's not in your home folder (ex: cd / )
- run the migration tool (on Ubuntu: sudo ecryptfs-migrate-home -u username)
- if it's successful, you can now press ALT+F8 to go back to the GUI and login
- run 'ecryptfs-unwrap-passphrase' and WRITE DOWN OR SAVE THE CODE IT RETURNS because you will need it if you ever have to pull your data off while the OS is not working. (You can run it again later if you need to, but run it now so that you can get your data if your Linux install gets botched.)
- run 'ecryptfs-setup-swap' to encrypt your swap partition (the encrypted folder data is not encrypted while it's in memory, and so if it's ever sent to the swap partition it can be stolen from there unless that too is encrypted - be aware that this will mean you cannot use Hibernate anymore, as the bootloader won't be able to restore the hibernation data)
(instructions from [1])
Mac
Backup all data (500MB)
Follow these instructions to backup all the bitcoin data (wallet and block chains) to an encrypted disk image.
- Open Disk Utility
- Click New Image and choose 500MB, 128-bit or 256-bit (faster or more secure) encryption and single partition.
- Save it somewhere you won't lose it (like your Wuala, Dropbox, Strongspace or whatever)
- Choose a safe and strong password
- Move everything from ~/Library/Application Support/Bitcoin/ to the image
- Symlink it back so the app would be able to use it
- ln -s /Volumes/Bitcoin ~/Library/Application Support/Bitcoin
Don't forget to mount your image before using Bitcoin and unmount after quitting it.
Backup just wallet.dat (40MB)
Follow these instructions to backup just the wallet.dat file. This results in a smaller disk image, but it's more complicated to do.
- Open Disk Utility
- Click New Image and choose 40MB, 128-bit or 256-bit (faster or more secure) encryption and single partition.
- Save it somewhere you won't lose it (like your Wuala, Dropbox, Strongspace or whatever)
- Choose a safe and strong password
- Move your wallet.dat file to the image
- Symlink it back so the app would be able to use it
- ln -s /Volumes/Bitcoin/wallet.dat ~/Library/Application Support/Bitcoin/wallet.dat
Don't forget to mount your image before using Bitcoin and unmount after quitting it.
Note: If you start the Bitcoin application without having the image mounted, the application will overwrite your symlink with a new wallet. If that happens, don't panic. Just delete the new wallet.dat, mount the image, and recreate the symlink like above.
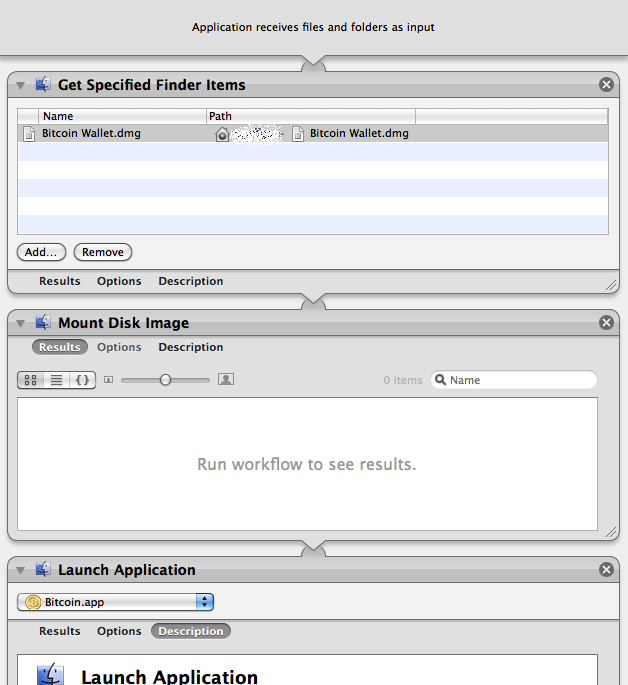
Automation: You can create a small application using Automator (included in OS X) to automatically mount the wallet and then launch Bitcoin App. See the Screenshot on how to do this.
Windows
If you are using Windows XP or Windows 7, you can keep your wallet on an encrypted disk image created by third-party software, such as TrueCrypt (open source) or Jetico BestCrypt (commercial). You can probably do the same with Windows Vista (but why would you use that?) or Windows 2000.
NOTE: You should configure BitCoin in this manner only on computers where you use BitCoin, but do not use that computer to mine. For example, this is a good configuration for a notebook or tablet computer.
Assuming that you have installed the Windows BitCoin client and run it at least once, the process is described below.
To mount the BitCoin data directory on an encrypted drive
- Use the third-party disk image encryption program of your choice to create and mount an encrypted disk image of at least 100 MB in size.
- Locate the BitCoin data directory, and copy the directory with all contents to the encrypted drive.
For help finding this directory, see Locating BitCoin's Data Directory.
- Create a Windows shortcut that starts BitCoin with the
-datadirparameter and specifies the encrypted drive and directory.For example, if you installed Bitcoin in the default directory, mounted your BitCoin encrypted drive as
E:\, and stored your BitCoin data directory on it asBitcoin, you would type the following command as the shortcut Target:C:\Program Files\Bitcoin\bitcoin.exe -datadir=E:\Bitcoin - Open BitCoin's settings and configure it NOT to start automatically when you start Windows.
This is to allow you to mount the BitCoin encrypted disk image before starting BitCoin.
- Shut down BitCoin, and then restart it from the new shortcut.
After doing this, any time you want to use BitCoin, you must first mount the BitCoin encrypted disk image using the same drive designation, and then run BitCoin from the shortcut that you created, so that it can find its data and your wallet. :-)
Locating BitCoin's data directory
The data directory is the location where Bitcoin's data files are stored, including the wallet data file.
Windows
Go to Start -> Run (or press WinKey+R) and run this:
explorer %APPDATA%\BitCoin
BitCoin's data folder will open. For most users, this is the following locations:
C:\Documents and Settings\YourUserName\Application data\BitCoin (XP) C:\Users\YourUserName\Appdata\Roaming\BitCoin (Vista and 7)
"AppData" and "Application data" are hidden by default.
Linux
By default BitCoin will put its data here:
~/.bitcoin/
You need to do a "ls -a" to see directories that start with a dot.
If that's not it, you can do a search like this:
find / -name wallet.dat -print 2>/dev/null
Mac
By default BitCoin will put its data here:
~/Library/Application Support/Bitcoin/
Backup
The only file you need to back up is "wallet.dat". Ensure that BitCoin is closed, copy this file somewhere else, encrypt it, and put it somewhere safe. Ideally, you would put this file in two places: one nearby, and one 100+ miles away.
You can use the backupwallet JSON-RPC command to back up without shutting down Bitcoin.
General Solutions
Your wallet.dat file is not encrypted by BitCoin. Anyone who can access it can easily steal all of your coins. Use one of these encryption programs if there is any chance someone might stumble upon your wallet.
- 7-zip - Supports strongly-encrypted archives.
- AxCrypt
- lrzip - Compression software for Linux and OSX that supports very high grade password protected encryption
- TrueCrypt - Volume-based on-the-fly encryption (for advanced users)
- WinRar - Commonly used archive software that supports verification records and encryption.
There is also a list of open source encryption software.
Password Strength
Brute-force password cracking has come a long distance, a previously thought secure password of random [a-Z] [0-9] [!-~] of 8 characters long can be trivially solved now (using appropriate hardware)... The recommended length is at least 12 characters long. You can also use a multi-word password. The Usability of Passwords
If you use keyfiles in addition to a password, it is unlikely that your encrypted file can ever be cracked using brute force methods, even 10 years from now when even a 12 character password might be too short.
Assume that any encrypted files you store online (eg. gmail, Dropbox) will be stored somewhere forever and can never be erased.
Storage of Archive
One of the most simple methods for storing a appropriately encrypted archive of your wallet.dat file is to send the archive as an email attachment to your own e-mail address. Services like gmail.com use very comprehensive distributed networks that make the loss of data very unlikely. One can even obfuscate the name of the files within the archive, and name the archive something less inviting, such as: 'personal notes' or 'car insurance'.
Another solution is to use a file storage service like Wuala ( encrypted, instructions), Dropbox and others, including the more secure SpiderOak.
Linux solution
Linux users can setup cron by running 'crontab -e' and adding this line:
01 */1 * * * /usr/local/bin/backupwallet.sh
This cron line runs backupwallet.sh at the 01 minute of every hour. Remember to add a newline after the last line of the crontab file, or else the last line won't run.
backupwallet.sh:
#!/bin/bash
TS=$(date "+%Y%m%d-%H-%M")
WALLET=/tmp/wallet${TS}
WALLET_E=/tmp/wallet${TS}.crypt
if
echo -n making backup...
bitcoind backupwallet $WALLET
[[ ! -s "$WALLET" ]]
then echo failed
elif
echo done
echo -n encrypting....
! gpg -r myusername --output $WALLET_E --encrypt $WALLET
then echo failed
elif
echo done
echo -n copying to distant server...
! scp $WALLET_E user@myserver.org:~/wallets/
then echo failed
else echo done
fi
rm -f $WALLET $WALLET_E
The shell script:
- Calls bitcoind backupwallet to create a time/date-stamped wallet.
- GPG encrypts the wallet with your public key.
- Copies the result to a backup location.
Restore
Assuming your backup is recent enough that you haven't used up all of your key pool... restoring a wallet to a new (or old) location and rescanning the block chain should leave you with all your coins. Just follow these steps:
- Quit bitcoin(d).
- Copy your backed up wallet.dat into your bitcoin profile directory.
- If copying into existing profile, delete file blkindex.dat and blk0001.dat to make the client re-scan the block chain.
And you'll be good as new.
Erasing Plain Text Wallets
A good practice is to keep at least two wallets, one as a "current account" for everyday transactions and one as a "savings account" where you store the majority of your Bitcoins.
The "savings account" wallet should be backed up in encrypted form only and all plaintext copies of this wallet should be erased. In case someone gains unauthorised access to your computer (either by physically stealing it or by exploiting a system vulnerability via the internet), they will only be able to spend the coins in your "current account" wallet.
In most operating systems, including Windows, Linux, and Mac OS X, simply deleting a wallet.dat file will not generally destroy it. It is likely that advanced tools can still be used to recover the wallet.dat file, even after it has been deleted.
The Linux shred command can be used to overwrite the wallet file with random data prior to deleting; this particular copy of the file will then be practically impossible to recover. Using shred (and similar tools on Windows) however does not guarantee that still other copies don't exist somewhere hidden on your HD. That will depend on your system configuration and what packages you have installed. Some system restore and backup tools, for instance, create periodic snapshots of your filesystem, duplicating your wallet.dat.
In Mac OS, clicking "Secure Empty Trash" in the Finder menu will shred the contents of the trash can. As with any OS this doesn't guarantee that there are not other copies elsewhere on your system.
For Windows, the built-in command cipher /W will shred all previously-deleted files. CyberShredder can securely deleted individual files.
eWallet
Storing bitcoins with an eWallet provider incurs risks as well. Basically you grant the third party, in this case eWallet, full access to your wallet.