Talk:Securing your wallet: Difference between revisions
No edit summary |
|||
| (7 intermediate revisions by 3 users not shown) | |||
| Line 18: | Line 18: | ||
Is it possible to still send money to my wallet, even if it's backed up and offline? Do bitcoins ever expire if they're not spent, or is there anything bad that can happen by not using my bitcoin client in a long time? [[User:Daniel.benoy|Daniel.benoy]] 23:18, 8 June 2011 (GMT) | Is it possible to still send money to my wallet, even if it's backed up and offline? Do bitcoins ever expire if they're not spent, or is there anything bad that can happen by not using my bitcoin client in a long time? [[User:Daniel.benoy|Daniel.benoy]] 23:18, 8 June 2011 (GMT) | ||
Technically your wallet does not hold bitcoins but rather the keys to those bitcoins. So whether you are online, offline, or dead is totally irrelevant to the Bitcoin network. They also never expire. The worst that can happen by not using it for a long time is that it will take a while to sync with the network. [[User:Lordcirth|Lordcirth]] 00:02, 28 May 2012 (GMT) | |||
== How often is it needed to backup the Wallet? == | == How often is it needed to backup the Wallet? == | ||
| Line 172: | Line 174: | ||
The first step is [https://help.ubuntu.com/8.04/serverguide/C/user-management.html to create a new user], which goes with the command: | The first step is [https://help.ubuntu.com/8.04/serverguide/C/user-management.html to create a new user], which goes with the command: | ||
sudo adduser <code> new_user_name </ code> | sudo adduser <code> new_user_name </code> | ||
On the message "Enter a new value or press ENTER for the default" one needs only to press the Return key. | On the message "Enter a new value or press ENTER for the default" one needs only to press the Return key. | ||
| Line 368: | Line 370: | ||
It may be worth it if someone would describe the correct procedure to secure the bitcoin wallet using MinorFs/AppArmor in a way similar to described in the above link for ssh keys without passphrases. | It may be worth it if someone would describe the correct procedure to secure the bitcoin wallet using MinorFs/AppArmor in a way similar to described in the above link for ssh keys without passphrases. | ||
= ‘Shred’ cannot always be assumed to be secure on modern filesystems! = | |||
I don't feel entirely comfortable with the suggested usage of the ‘shred’ command in the given Linux script. My understanding (and according to shred's manpage) is that on modern (especially journaled) filesystems, there is ''no'' guarantee that when an application like shred asks the OS to overwrite a file, that the file will actually be physically overwritten in place on the disk. Unless there have been features implemented to allow special handling by the kernel for such security applications (I haven't investigated, so maybe there are, or maybe not), it would probably be safer to disable all system swap (i.e., with ‘swapoff’) and then store the unencrypted data on a temporary RAM disk only, then unmount the RAM disk afterwards to ensure it never gets written to disk. I've done this before, though unfortunately it's a bit of a hassle and normally requires running commands that need root privileges or sudo, etc. Comments? | |||
~ [[User:Ijel|Ijel]] 03:49, 11 February 2012 (GMT) | |||
@Ijel Well, TrueCrypt uses RAM-only storage when mounting a file. I'm pretty sure it has anti-swap protection too. [[User:Lordcirth|Lordcirth]] 23:55, 27 May 2012 (GMT) | |||
== Automated backup: inotify v.s. cron == | |||
Hi, what would you think about a an automated backup using inotify (or pynotify: http://pyinotify.sourceforge.net/doc-v07/) to monitor writes on the wallet, which trigger the backup. It would save space by not copying the same versions of a wallet, and not wait for the next cron iteration to backup the wallet (which could be lost in between). --[[User:Mammique|Mammique]] ([[User talk:Mammique|talk]]) 06:17, 25 September 2012 (GMT) | |||
:There is also lsyncd: http://code.google.com/p/lsyncd/--[[User:Mammique|Mammique]] ([[User talk:Mammique|talk]]) 06:20, 25 September 2012 (GMT) | |||
Latest revision as of 06:20, 25 September 2012
The article is too huge. The Mac solution does not scale; the suggested sizes are too low and the maximum size is infinite. X 17:10, 8 January 2012 (GMT)
This article needs a rewrite following the introduction of the Bitcoin.org client's ability to passphrase protect the keys in the wallet. Perhaps some sections also -- something like "typical consumer use" (where the client's encryption is adequate) and "commercial-grade protection" where the topics such as encryption at the filesystem is addressed. - Sgornick 10:24, 28 December 2011 (GMT)
The five paragraphs in Technical Background all say the same thing. --Mcandre
Note: the backupwallet.sh script in the linux section doesn't actually work. I suspect it is caused by the wiki changing the formatting. I wrote my own version that uses much more standard shell syntax.
Wscott 11:28, 11 February 2011 (GMT)
I fixed the backupwallet.sh script. It just needed a nowiki tag around a conditional statement. -- Mweather 23:48, 20 May 2011 (GMT)
The approach for "Making a secure workspace" seems to differ greatly for linux and mac. Why? It seems like if you are going to make firefox secure, which is basically all the linux section recommends, you would want to do that on a mac too. And the recommendation in the mac section to keep the wallet in an encrypted volume with a symlink in the expected system location should be done on a linux box too, shouldn't it, like using truecrypt or something... Am I wrong??? Can someone with advanced knowledge please advise...? Also, if you want bitcoin to run all the time in the background on linux, but you have it set up in a separate user from your main user account, well, you are out of luck? Can justifications and explanations be added to the recommendations, and also I guess some alternatives with pros and cons be offered, for people with different needs and computing situations. Thanks! --GusGustavo 13:33, 26 May 2011 (GMT)
Time Sensitivity
Is it possible to still send money to my wallet, even if it's backed up and offline? Do bitcoins ever expire if they're not spent, or is there anything bad that can happen by not using my bitcoin client in a long time? Daniel.benoy 23:18, 8 June 2011 (GMT)
Technically your wallet does not hold bitcoins but rather the keys to those bitcoins. So whether you are online, offline, or dead is totally irrelevant to the Bitcoin network. They also never expire. The worst that can happen by not using it for a long time is that it will take a while to sync with the network. Lordcirth 00:02, 28 May 2012 (GMT)
How often is it needed to backup the Wallet?
Is it necessary to make a backup after each transaction? This page is not clear about this. Please add this information to the page!
Creating a New Wallet
This section isn't helpful; it tells you when to create a new wallet, but not how. I'm a new user, and the wallet was created when I installed the BitCoin program. I will find out how to create a new wallet, and then edit this section so that it actually explains the task that it sets out to explain. :-) ErgoOne 15:19, 9 June 2011 (GMT)
Making a secure workspace
For me space needed in ~/Library/Application Support/Bitcoin (Mac) is more than 400MB (!) after having loaded all blocks from bitcoin app. So 100MB is much too small (may be sufficient for just wallet.dat, but then the steps to do had to be changed). Hartrock 18:48, 12 June 2011 (GMT)
I updated the wiki steps to just backup wallet.dat --ChocoboLee 19:18, 15 June 2011 (GMT)
Flaws with argument regarding encryption
Can someone please explain to me how encrypting your wallet will actually protect against a trojan stealing it. Because once you mount the encrypted file, and decrypt it not only can bitcoin see it but the trojan can as well. This strategy seems to work only in the following circumstances: 1. The wallet that has the majority of your cash you never decrypt when you have an open internet connection. 2. Assumes that a trojan only operates when an internet connection is present and it can transmit the wallet data file.
Even if you were paranoid and never were connected to the internet when the wallet file with the bulk of your funds was decrypted this still would not solve the problem. In the event that a trojan seeks to copy your wallet file to another location on your computer it could wait for an open internet connection to transmit this data. So even if you reencrypt the wallet file before connecting to the internet this type of trojan has already made a copy of the decrypted file and can transmit it as soon as an internet connection becomes available.
Also how in the world could you ever use this wallet to transfer cash to another user if you are offline? Maybe I don't understand how bitcoin works but don't you need to be online in order to transfer bitcoins? Basically the bottom line is that bitcoin cannot read an encrypted wallet file which means that in order to use the wallet you need to decrypt it which means its vulnerable to trojans who can steal it the moment you want to use it.
This seems to be a fundamental flaw in this discussion "securing your wallet" Why doesn't bitcoin just address this in the software allowing for the wallet to always be encrypted and require a password upon startup. If you want bitcoin to go mainstream I don't understand why you can't address this fundamental flaw that would be solved by an always encrypted wallet file that the software can read and write to.
- The fundamental flaw is trying to secure the wallet when the whole system is already technically compromised. It does not help to have a secure wallet then. What a trojan could do is, for example, to replace the bitcoin client by a sligthly changed one that usually works as expected, but once in a while sends the money to an address which is owned by the attacker. The people you think you pay will become angry because the money you think to send never does arrive at them. Of course, the malicious client can be intelligent enough to wait until the is some real amount of coins in the play. One day you'll think you bought a car but the money is somewhere else. The same applies, for example, if the payment addresses you receive are modified by some malicious e-mail program.
- So what is the bottom line? Encrypting the wallet helps against a roommate stealing your coins if he has two minutes of physical access to your computer. It helps against burglary and forgetting the laptop in the train. It generally does NOT help against compromise of the system. The whole system must be kept safe, not just the data in the wallet. And this is not something that the bitcoin software is responsible for. It is the responsibility of the user to install and maintain a secure system. It is a fundamental fallacy to expect that a certain piece of software should still work as the user expects if the whole system is not any more under the control of the user. In this sense, bitcoin can not go mainstream. Instead, main stream users need to reach some point of mental sanity. --Joise 09:14, 14 August 2011 (GMT)
Added a new entry to backup methods
WalletPaperbackup Is a great way to get your wallet out of the digital world and onto paper --Jrwr 02:02, 24 June 2011 (GMT)
Unsecure suggestion for passwords
Especially with Bitcoins the Password advice from Gibson Research is dangerous because passwords must also be safe in the future when it comes to wallet storing. This is definitely not given with this system. It might be true, that with today's brute-force tools, the "d0g..........." pw is safer than hkjhHZ756s=&g%7 but in the very near future (maybe already exists) there will be new tools, that will find out, what kind of simplifiers are often used by humans and will combine brutforce with simplifiers and thus come to "d0g............" very quickly!
Section 4.2
If you recommend that one backup wallet.dat on a mac via creating an encrypted image file, don't you think you should also remind the user to backup his ~/Library/Keychains directory? There is little point in backing up wallet.dmg on Wuala or whatever if you lose your AES key to the image, and the scenario when you need to recover wallet.dmg is probably the scenario where you've also lost ~/Library/Keychains... e.g. laptop stolent, etc.
Back-Translation of German Version
Hi,
I have translated the page to the German Version, expanded it by several points and concepts which seem important to me - namely, a disticion between data confidentality, system integrity and the notion of technical compromise, and adapted the ordering according to these concepts. Here is the back-translated version as a suggestion what could be expanded. I've translated it quickly using Google Translate, that means wording and style can't be expected to be perfect. Nevertheless, I hope it's helpful. --Joise 09:14, 14 August 2011 (GMT)
Introduction
The security of the wallet can be divided into two separate objectives:
1. Safeguard against loss
2. Secure against theft
In the case of a currently not adequately secured wallet (eg with a weak password uploaded on the Internet):
3. New, create a mew secure wallet (with a reasonably long password)
Technical background
The important first objective of the design of the wallet is protection against data loss. The personal bitcoin wallet has a pool of queued keys stored in a file named wallet.dat. The default number is 100 keys in the Key pool. The number of can be adjusted with the "-keypool" parameter in the command line. If for some reason you need a new address, it is not generated on the fly, but taken from the pool. A new key is then created to fill the pool back to 100 keys. If a backup is first created, it contains all used keys plus 100 unused ones. After a transaction, 99 unused keys remain. After 100 operations which require a new key, new keys are used, which are not present in the backup. Because the backup does not have these new keys, this backup can possibly lead to a recovery loss of Bitcoins if the wallet file is destroyed, for example by a head crash.
The safety of deposits in Bitcoin depends on three conditions:
- The confidentiality (secrecy) of the private key for the entire time from initial production to final use
- The integrity of the software on the system used.
- As well as the protection from loss of wallet eg by failure of the hard disk
The bitcoin software assumes (for very good reasons) that integrity and confidentality of the computer and user account is intact. The reason for this is that, strictly spoken, securing the computer is not the business of some application software like bitcoin. A computer which has not both its confidentiality and integrity ensured, is compromised. This means, that it can not longer be excluded that Bitcoins are stolen. A computer on which malware in the form of some trojan is installed or which runs any virus, is always compromised. All data - including the bitcoin wallet - could be "stolen". On the other hand - and this is far more far-reaching and important - the other software on the computer is absolutely no longer under control of the user. A compromised system can only be brought back to a safe condition if it is completely erased, fully installed with a fresh operating system and all new security updates are applied. A "disinfection" of virus-infected programs is not enough! Erasing the old, compromised system can also mean it is necessary to flash the BIOS and do a BIOS update - there is some malware which modifies the BIOS.
A password that belongs to a data backup must be permanently protected from loss just like the files themselves, otherwise in case of doubt the backup is worthless.
Securing the confidentiality and integrity of the Wallet and Software
Creating a New Wallet
In the event that the wallet was possibly or actually stored in a compromised state, or spreaded, it is wise to create a new wallet and to transfer all money amounts in the old wallet to the new. Once this is done, someone who has attained knowledge of the old private keys, can not longer use them to steal bitcoins. Keep in mind that leaked keys can be used much later from their generation. For example, if you generate some keys to day, transfer them to a new computer in three years, and throw the old computer in ten years to the trash, and it still contains keys that you have created today, these could still be used to access bitcoins that you received in the meantime.
Creating a new wallet can be useful, for example, if someone has saved a wallet with a password of 12 characters for a service online. Meanwhile, passwords with 12 up to about 15 characters are decoded and the private keys are no longer safe. The strategy only to re-encrypt the wallet is not enough, because the keys are not safe.
Creating a safe and secure work space
Large and complex programs like Web browsers are never completely safe. Therefore, it is extremely useful, not to run the Bitcoin client program with the user identity that you use to surf the Web or read e-mails. The modern operating systems can isolate applications for different user IDs from each other quite effectively, and this is a huge advantage to security.
Digression: Secure Passwords
Passwords
A proven method for producing safe, but still learnable passwords goes as follows:
- Make up a nonsense phrase like
"Thirty crows fly backwards to the moon, but they do not have a ticket."
The more bizarre the sentence, the better you remember it.
- The first letters and numbers are used for the password:
30CfbwttM,btdnhaT
- Now we get creative and replace a few characters, eg "A" looks like but like "4":
30Cfbw2tM,b|dnh@T
- Now insert one or a few signs that are not found on English keyboards (Tips):
3ß0Cþfböw2tM,b|dnh@฿T
Strong passwords are now, where huge computing resources like hashed databases and botnets are available for cracking, about 15 to 20 characters long. Few people can remember so long passwords error-free, especially if they make some longer holiday. Therefore, write to the password and put it in his wallet. (That's still heretical but I have a good Reference - Bruce Schneier [1])
- To protect against unauthorized use of the written down password one should append some characters that you really have in your head.
Now it is so that a forgotten password is at least as bad as a cracked. A button labeled "Forgot your password, sent new by e-mail" does not exist in Bitcoin. So the consequence of "Password away" is inevitable "money away ". Don't forget that!
- The written-down password should be preserved in something like a bank deposit box (can be rented for a few bucks yearly) or in a fireproof safe. I you have USD 100,000 in BTC, you want to have a fireproof safe if your house has burned down. Believe me.
Passphrases (password phrases) or mantras
- An alternative to passwords which has at least the same strength against techniques like rainbow tables, but is in comparison much easier to remember is the use of pass-phrases or a "mantra". The required length depends on the use. Passphrases for online services may be safe enough with four common words. Secure passphrases for files (which can be rapidly tried off-line) should contain at least six unusual words and at least 35 characters in length. This comic by XKCD explains the principle.
- An example sentence would be: "The Lemon flambé the okapi a phosphorescent absolution."
- Much of the strength of this method relies on technical reasons: Once a password has reached a certain minimal complexity, the fastest way to crack the password is a brute-force search with rainbow tables and charts. And since for this methods, the length of the password is the decisive factor, long pass phrases, which are comparatively much better to remember, win over short very complex passwords (which are hard to remember but easier to crack).
- In-depth information on passphrases here: passphrase FAQ by Randall T. Williams.
- Warning: Completely unsuitable are fixed expressions and popular idioms. Don't use any meaningful sentence and anything that might be published on the web.
Special Linux distributions
To secure a Windows system comprehensively is a complex and difficult task. Securing which is appropriate for the administration of five-figure amounts requires knowledge which the average user does not have.
As an alternative, there are some special Linux distributions. Using them, one can create a secure space specially for Bitcoin, and they require almost no setup:
- c't Bankix, a distribution for online banking, is a adapted and, of course, free version of Ubuntu that was created by the renowned German Heise magazine publisher. Following to the (important) first update the system will be put on a read-only medium and cannot longer be manipulated by unauthorized changes to the software.
- Damn Small Linux is a popular, small Debian-based Linux, which contains only the most important functions and thus provides less attack surface. The derivation from Debian guarantees speedy and thorough security updates.
- Knoppix is a popular live-CD distribution with excellent hardware detection, which has a slightly larger footprint than Damn Small Linux, and a number of interesting features. For example, it offers support for blind and visually impaired persons.
- LinuxCoin, many additional functions for mining
The following distributions are suitable only for users with good knowledge. However, their excellent safety features makes them quite interesting starting points for Bitcoin Appliances:
- Tin Hat Linux is a Hardened Gentoo derivative. In addition to a very small size and a very comprehensive encryption it has interesting additional security features, such as Grsecurity.
- Alpine Linux uses, similar to Tin Hat Linux etc. Kernel functions with Stack Smashing Protection. It uses instead of the standard glibc the uClibc, which means that the Bitcoin client needs to be compiled specifically for this distribution.
Linux
Protected user account
The first step is to create a new user, which goes with the command:
sudo adduser new_user_name
On the message "Enter a new value or press ENTER for the default" one needs only to press the Return key.
Then do you register as a new user, eg "Switch User" with (at Ubuntu in the menu to log off). If you are logged in, we search for the file manager, select this from the home directory (with the house icon), then right-click "Properties", then the access permissions. Here you select "Other" and set the permissions to "nobody". With this step, other programs can not read the other user's wallet.
The newly created user should be safe to use in order to keep him safe, exclusively for Bitcoin.
There is also a good idea to encrypt this user's home directory with the package ecryptfs-utils.
- If the home directory is not empty, first backup it to some other medium.
- Now install ecryptfs-utils (Ubuntu: sudo apt-get install ecryptfs-utils)
- From X11 (graphical system) log and log in with Ctrl + Alt + F1 in the Linux console - if you are logged in X11, the home directory is encrypted.
- The current directory change so that it is not in the home folder, eg "Cd /".
- The migration tool to run: (in Ubuntu: sudo ecryptfs-migrate-home-u username)
- If it succeeds then you can press ALT + F8 to go back and log in X11.
- Run the command 'ecryptfs-unwrap-passphrase'. Without exception write and store the code that you receive on a secure medium. Without this code no data - including the wallet - can be accessed if the system does not work'
- Run the command 'ecryptfs-setup-swap' run, which encrypts the swap partition. Otherwise, keys in your purse in plain text can go to the the swap partition where they might be stolen. This unfortunately also means that "idle" or Hibernate can not be used anymore because the bootloader can not restore the dump. An more conventient alternative is to overwrite the swap partition when you shut down the machine (after the deactivation of virtual memory) with random data.
(Instructions from # Migrate)
For more information
Windows
- Create an extra user, under which only the Bitcoin software is running. So the wallet is somewhat protected from malicious code in applications for other users:
Browser Security
Firefox
To secure the browser, you start Firefox, go to menu "Edit" (edit), and select "Preferences" (Settings).
- Now you start with the tabs on the left, select the "Startup" option "Show a blank page" (Clean Slate).
- By "content" (content)
- The option "Load images automatically / Load images automatically" opt out,
- Also "Enable Javascript Enable / javascript" opt out.
- In the tab "privacy / data protection" in the "History / History History," select "Never remember history" / "do not save history".
- In the tab "Security" in the "Passwords"
- The "remember passwords / passwords save" deselect
- Also "use a master password" / "master password".
- Finally, in the tab "Advanced" / "Advanced" option
- "Automatically check for updates" deselect
- As "add-ons" and
- "Search engines" / "search engines" opt out.
If Javascript is disabled, the page linux download page] to download new versions of the Bitcoin Clients will no longer automatically download, so you have to link to the "direct link" on notice "Problems with the download? Please use this 'direct link' or try another mirror." . click Once you make the effort made, of course you checked the download of new clients Bitcoin the checksums, which are indicated on the sourceforge page, with the program sha1.
Protect against data loss: Backup
Secure the only file you need is the wallet.dat. Advance to make sure that Bitcoin not running anymore! The best way would be to encrypt the file and store somewhere safe.
You can also backupwallet JSON-RPC command used to create a backup on the fly.
Where to find the Bitcoin folder
The Bitcoin folder is the folder where the data is wallet.dat along with the file.
Windows
Click on "Start", then Run and enter this:
- % APPDATA% \ Bitcoin
A folder should open now, for most it would be:
C: \ Documents and Settings \ username \ Application Data \ Bitcoin (XP) C: \ Users \ username \ appdata \ roaming \ Bitcoin (Vista and 7)
Linux
Bitcoin should create a hidden folder in your home directory of the running user.
~ /. Bitcoin /
It should not be there, it can be possibly due Find /-name wallet.dat-print 2> / dev / null . find Or as root
- Updatedb
followed by
- Locate wallet.dat
The handiest backup method under Linux is probably the copy on one or more wallet.dat used for USB flash drives or memory cards that are kept in a safe place (fireproof safe, bank safe, aquarium with piranhas, etc).
Individual encryption of the wallet.dat file
- For individual encryption of the purse, the available cross-platform programccrypt is well suited. It encodes a variant of the AES Rijndael algorithm. a recognized standard, which is considered very safe. The plain-text version of Wallet.dat will be replaced automatically. As with all strong encryption, a careful backup of data and keys is essential - under Linux, the risk of loss due to forgetting the key is much higher than by computer intrusions and malware.
- For automatic storage of encrypted copies GnuPG (Gnu Privacy Guard) is well suited. To encrypt data, ones need only the public key. Only to decrypt a backup, the private key is used, which can be stored otherwise in a safe place. Using a fixed pair of keys reduces also the risk of loss of a key by unnoticed typos when typing them.
- Additional protection against attacks by key loggers provide smart cards and hardware tokens like the Crypto Stick the Deutsch Privacy Foundation or the GnuPG Fellowship smart card. The special advantage is that you GnuPG keys that are very safe due to their length, and can be stored on the smart card. A six-digit PIN code protects the contents of the smart card. If it is entered incorrectly multiple times, then the content will be deleted. instructions here.
- Together with the FUSE-based file system EncFS can you also back up individual files as wallet.dat individually. The entire list can Bitcoin but are not used because the database is encrypted with EncFS.
Mac
Note: The following instruction are not checked due to lack of hardware. Please check and correct if necessary, then remove the note!
The directory containing the Bitcoin wallet.dat is usually here:
~ / Library / Application Support / Bitcoin /
Secure all data (500 megabytes)
These steps (chain wallet and block) of all data stored on Bitcoin an encrypted disk image:
- Disk Utility Open
- Click on "New Image", 500MB, 128-bit or 256-bit (faster or more secure) encryption specify eintelne partition.
- Copy in a place where you will not lose the image (eg Wuala, Strong Space ofer whatever)
- A strong and secure password select
- Copy everything from ~ / Library / Application Support / Bitcoin / in the image
- Create symlink to the old place, so the app can benuutzen it
- Ln-s / Volumes / Bitcoin ~ / Library / Application Support / Bitcoin
Do not forget to mount the image before using Bitcoin and unmount afterwards.
Backup file wallet.dat purses alone (40MB )
These steps only protect the file wallet.dat. This causes a small memory dump, but is more complicated.
- Disk Utility Open
- Click on "New Image", 40MB, 128-bit or 256-bit, single select partition.
- Store in a place where you will not lose the backup.
- A secure and strong password, select
- The file wallet.dat move in the image
- Create symlink to the old place, so the app can find and use the file
- Ln-s / Volumes / Bitcoin / wallet.dat ~ / Library / Application Support / Bitcoin / wallet.dat
Do not forget to mount the image before using Bitcoin and unmount afterwards.
Note: If you start the application Bitcoin without the image is mounted, the program is the symlink (a kind of shortcut) wallet.dat with the new one. Do not panic! Rename the new order wallet.dat or delete it, mount the image, and just put a new symlink. The old wallet.dat may of course be canceled under any circumstances.
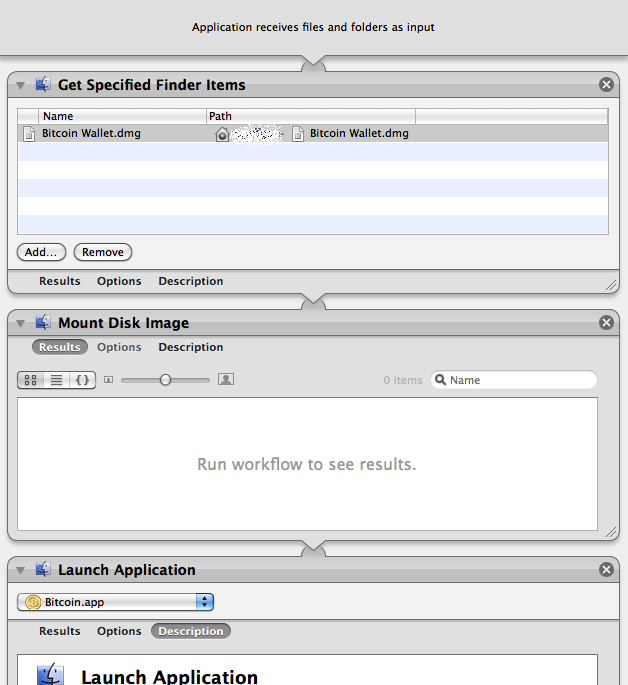
Automation: The program 29% 28software Automator (included in OS X) can automatically mount your wallet and start Bitcoin App.
Alternatively, the following shell script can be used to decrypt wallet.dat which automatically starts the Bitcoin client, and they subsequently re-encrypted. The script works for sowoghl for OSX and Linux: Bitcoin-launch-script
General solution
wallet.dat is not usually encrypted, everyone who has access to the file, can freely dispose of the coins. You can encrypt your wallet.dat with one of these programs, should there be the slightest chance that someone else has access.
Note: Encryption does not protect the wallet against security risk after they have occured. Encryping a wallet after finding a computer virus or a trojan helps absolutely nothing. Also, encryption does not help against the complete loss of control which a system compromise means.
Encryption with Smart Card
Folders can be encrypted with GnuPG-compatible smart card. A very secure solution is to stick the Crypto Deutsch Privacy Foundation:
Storing the Archives
A backup on Flash Media / Memory Sticks and storing them in secure locations is a reasonable solution.
BOTG: Bitcoin Off The Grid
- Another alternative that is suitable for high security requirements,is "BOTG - Bitcoin off-the-grid" see info in the announcement to LinuxCoin. It is a script that can create a key pair without Internet connection. As the private keys are created on a system that does not have Internet access, and are stored offline, they can not get lost via the Internet. The public key can be passed on and received as normal transactions that can be looked up in block Explorer. Only if you want to use the fund, you must import the private key into a Bitcoin client. From then on, the normal safety precautions apply.
Securing your wallet on Ubuntu and/or Suse
For users that use a Linux system that comes with AppArmor, it is probably possible to use the MinorFs system with a procedure not unlike that described here for secure ssh without a passphrase:
http://minorfs.polacanthus.net/wiki/Ssh_private_keys_without_passphrase
Its a bit of a hack, but it would make it impossible for malware running under the same user id as bitcoin to gain access to the wallet.
It may be worth it if someone would describe the correct procedure to secure the bitcoin wallet using MinorFs/AppArmor in a way similar to described in the above link for ssh keys without passphrases.
‘Shred’ cannot always be assumed to be secure on modern filesystems!
I don't feel entirely comfortable with the suggested usage of the ‘shred’ command in the given Linux script. My understanding (and according to shred's manpage) is that on modern (especially journaled) filesystems, there is no guarantee that when an application like shred asks the OS to overwrite a file, that the file will actually be physically overwritten in place on the disk. Unless there have been features implemented to allow special handling by the kernel for such security applications (I haven't investigated, so maybe there are, or maybe not), it would probably be safer to disable all system swap (i.e., with ‘swapoff’) and then store the unencrypted data on a temporary RAM disk only, then unmount the RAM disk afterwards to ensure it never gets written to disk. I've done this before, though unfortunately it's a bit of a hassle and normally requires running commands that need root privileges or sudo, etc. Comments? ~ Ijel 03:49, 11 February 2012 (GMT)
@Ijel Well, TrueCrypt uses RAM-only storage when mounting a file. I'm pretty sure it has anti-swap protection too. Lordcirth 23:55, 27 May 2012 (GMT)
Automated backup: inotify v.s. cron
Hi, what would you think about a an automated backup using inotify (or pynotify: http://pyinotify.sourceforge.net/doc-v07/) to monitor writes on the wallet, which trigger the backup. It would save space by not copying the same versions of a wallet, and not wait for the next cron iteration to backup the wallet (which could be lost in between). --Mammique (talk) 06:17, 25 September 2012 (GMT)
- There is also lsyncd: http://code.google.com/p/lsyncd/--Mammique (talk) 06:20, 25 September 2012 (GMT)